Cyber security
Cybersecurity Programs Struggling To Keep up With Attack Surfaces, Risk Priorities in Pandemic Conditions
A new report from attack surface management firm Randori indicates that cybersecurity programs are struggling to manage attack surfaces that have become significantly more difficult due to pandemic conditions. Chief Information Security Officers (CISOs) report that organizations are mixed on security spending, and that prioritizing risks and patching is a consistent problem.
Pandemic increases risk tolerance
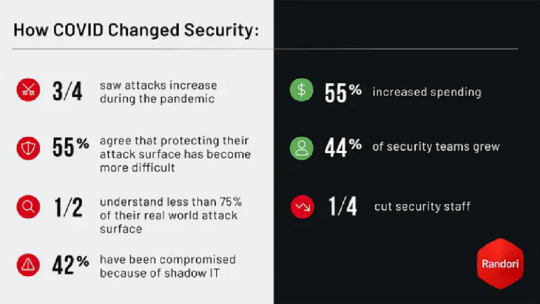
The report indicates that CISO appetite for risk tolerance is increasing due to pandemic realities. 76% of those surveyed felt that breaches were inevitable, and about 65% felt that certain assets could be compromised without the organization’s brand being harmed. However, that doesn’t necessarily imply that decision-makers know what to prioritize. 67% said they have trouble determining what to patch first. And 85% said that they feel they have a clear picture of the organization’s attack surface, but 48% also said that they are aware of no more than 50% of that surface.
While the threat categories of 2020 are not all that different from recent years, the volume of attacks (and amount of pressure on CISOs) has increased substantially. Remote work and cloud migration in response to the pandemic are responsible for the bulk of this pressure, as is “shadow IT” rigged up by the remote workforce in response to these new challenges. Most organizations did increase spending to deal with these new challenges, but that spending did not necessarily translate into better overall security outcomes.
The report indicates that shadow IT is perhaps being underestimated as a source of vulnerability for cybersecurity programs. 42% of the 400 survey respondents said that it had caused compromise in the previous year.
What is the increased spend on cybersecurity programs brought on by the coronavirus outbreak going to? In addition to the 44% of organizations that said they had brought on more staff during the pandemic, 52% said that they purchased new software. However, 84% said that they are only using vulnerability management solutions to manage the attack surface; the majority do not make use of an attack surface management product.
Cybersecurity programs adapt to expect data breaches
The overwhelming majority of security leaders now assume that as long as pandemic conditions and trends persist, breaches are going to happen at some point. The name of the game seems to be adapting cybersecurity programs to a harm reduction approach. Decision-makers are focusing on securing the most sensitive information from intruders and ensuring that organizational reputation damage is kept to a minimum.
However, the majority also appear to not be entirely clear on the best security strategies to get that done. 82% said that they need better solutions for prioritization, in addition to the 76% that felt prioritizing patches had become too hard to adequately keep up with. Security leaders know what changes they need to make to their cybersecurity programs, but they’re still grappling with exactly how to do it.
All indications are that this “new normal” for cybersecurity programs is not going away once the pandemic does. The work-from-home trend is expected to continue even after the virus situation subsides, and cloud migration moves are unlikely to be undone. Randori believes the central problem at present is that security experts simply do not know what is exposed to cyber attacks and what the relative network security risk levels are given this flurry of fairly rapid changes.
Are attack surface management products a solution for struggling cybersecurity programs?
They can be if they improve visibility into the complete attack surface. One source of this general confusion about priorities and risks is that many organizations have a patchwork system of security products and processes in place. A focus on directly protecting critical assets can create blind spots elsewhere, particularly in terms of third-party vendor access. Baked-in legacy tools and processes might also not be up to keeping pace with the constantly evolving threat landscape. And while regular penetration testing certainly helps, it is not a cure-all given the high cost that would be required to cover the full range of the possible attack surface.
SOURCES: Randori - CPO Magazine - Author: Scott Ikeda
 .
.